-
Product Management
Software Testing
Technology Consulting
-
Multi-Vendor Marketplace
Online StoreCreate an online store with unique design and features at minimal cost using our MarketAge solutionCustom MarketplaceGet a unique, scalable, and cost-effective online marketplace with minimum time to marketTelemedicine SoftwareGet a cost-efficient, HIPAA-compliant telemedicine solution tailored to your facility's requirementsChat AppGet a customizable chat solution to connect users across multiple apps and platformsCustom Booking SystemImprove your business operations and expand to new markets with our appointment booking solutionVideo ConferencingAdjust our video conferencing solution for your business needsFor EnterpriseScale, automate, and improve business processes in your enterprise with our custom software solutionsFor StartupsTurn your startup ideas into viable, value-driven, and commercially successful software solutions -
-
- Case Studies
- Blog
A Full Guide to Ecommerce Website Security
Ecommerce companies put a lot of effort into protecting their users’ personal information from breaches. However, there are many other aspects that also matter for ecommerce site security. In this article, we provide you with a complete security checklist that will show you how to secure your ecommerce website.
Most common security threats
Before we proceed to the list of website security checks, we’d like to point out the security threats ecommerce websites most frequently experience.
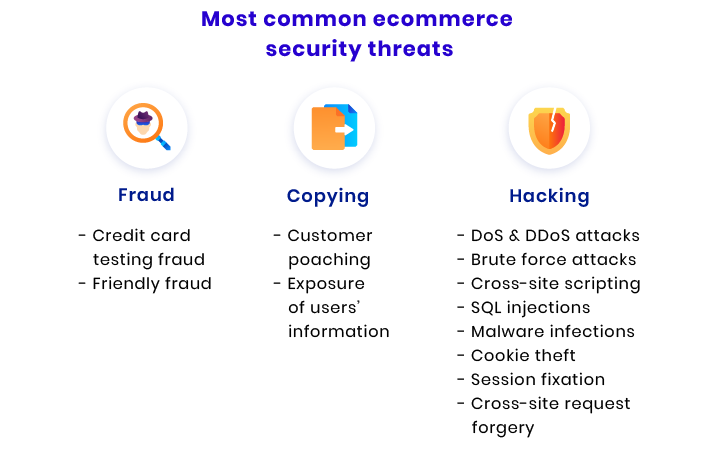
Fraud
Fraud is a deceptive and malicious activity with the intention to obtain a benefit from the victim. Ecommerce is prone to financial machinations connected with credit card testing and friendly fraud. Let’s figure out what these types of fraud are about.
Credit card testing fraud
Credit card testing is when malicious actors use stolen or lost credit cards to order items on ecommerce platforms or online shops to see if the cards are aсtive. When trying to crack or test credit cards, fraudsters make small purchases. If the payment goes through, they start making big and costly orders.
Identifying card testing is easier when you have a well-thought-out order management process. The major indicators of credit card testing activities on your ecommerce website are the following:
- Increase in declines. When testing numerous credit cards, there’s a high chance that most cards will be declined since their real owners have blocked them.
- Spike in the number of small orders. When testing credit cards, fraudsters not only test if the cards can be used; they also test the credit limits. That’s why when your website is a victim of credit card testing activity, the number of small purchases increases within a short period of time.
- Increase in orders made from foreign IP addresses. If you run a small local business, an increase in the number of buyers from abroad can be a reliable indicator of credit card testing activity.
Friendly fraud
Friendly fraud is a type of fraudulent activity fraudsters use to get items from your ecommerce store for free. With friendly fraud, a malicious individual orders your products under the guise of an ordinary buyer. However, when the order is completed, the buyer contacts the payment processor to claim that the transaction was invalid and to request a chargeback.
Fraudsters make their claims sound honest. For instance, they can say that the item was never delivered or that they actually canceled the order but your ecommerce website still charged them money. If the payment processor performs the chargeback, your company will be the one that needs to pay the order amount to the payment processor.
Copycats
Copycats are individuals or companies who create a copy of your website or application, content, or brand. Copycatting usually aims to poach your customer base by simply creating a website that looks just like yours so your users can’t notice the difference.
Unfortunately, it’s impossible to completely prevent your website from being copied. However, there are ways to make copying much more troublesome for copycats:
- Disable text selection. This will make it harder for copycats to copy your website’s content.
- Turn off copying with the Ctrl + C and Command + C keyboard combinations. Having these shortcuts turned off on your website pages will make copying much more complicated for malicious users.
- Disable mouse right-clicking. After switching off right-clicking, you’ll leave no chance for copycats to easily copy your content.
- Register for trademarks and copyrights. With trademarks and copyrights, when you come across a company that imitates your website or uses your name, logo, or other brand attributes, you’ll have a legal basis to sue for illegal use.
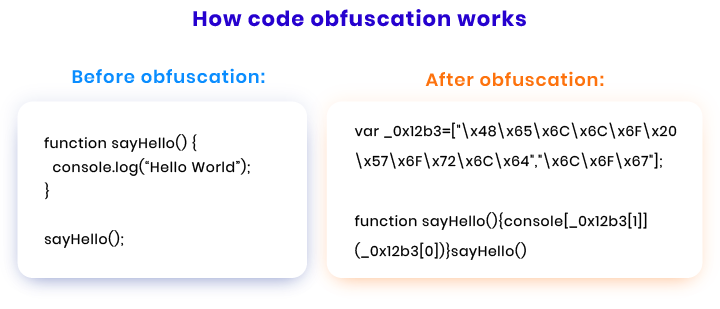
If you have a mobile application, there’s a risk that your users’ data may be stolen by means of copying the application’s source code. That’s why it’s best to protect your app with the help of code obfuscation. Code obfuscation is the act of deliberately making code difficult for humans to understand and useless for intruders.
Here’s an example of how code obfuscation works.
Hacking attacks
Hacking attacks are malicious actions performed with the intention to steal your or your users’ information, hinder your website’s performance, and make a profit. Let’s review the most common hacking attacks ecommerce websites face.
DoS & DDoS attacks
Denial of service (DoS) and distributed denial of service (DDoS) attacks generate fake traffic to disrupt normal traffic to your website and exceed its capacity to handle requests. The difference between the two is that in the case of a DoS attack, the fake traffic is coordinated from one device, while in a DDoS attack, multiple devices are used.
Brute force attacks
A brute force attack uses a trial and error method to gain access to a website’s admin panel. With the help of software applications and tools, hackers try to find the right login and password combination for your website’s admin account.
Cross-site scripting
Cross-site scripting is a code injection attack that influences your website’s users. Hackers can use website vulnerabilities to compromise users’ interactions with a website. Usually, attackers place malicious code on an ordinary web page, and once a user visits the page, the code is executed. After that, hackers can perform any available actions on the user affected by the injection and access any of the user’s data. Moreover, if the injection affects the website admin, hackers can access the website’s functionality and data.
SQL injection
SQL injection is one of the most commonly used web hacking techniques. It occurs when a malicious user inputs a SQL statement instead of the input your website expects. SQL injection helps hackers bypass your website security measures and also retrieve, add, and change records in your database.
Malware infection
Malware infection is a collective term that covers viruses, worms, Trojans, ransomware, and spyware. Each type of malware has its specifics and can influence your website and users differently. Malware can steal your and your users’ data, erase information, or block access to your own files.
Cookie theft
Cookies are quite useful for both website users and website owners. However, hackers can make use of cookies as well. After stealing your users’ cookies, hackers can easily access users’ accounts on your website and use credit card information as they wish.
Session fixation
A session fixation attack happens when a hacker obtains your user’s session ID and uses it for personal gain. To get a valid ID, an attacker prompts valid users to click a link that redirects them to the login page and then provides the attacker with the session ID. When using this ID, attackers can send malicious requests to the web server as if they were valid website users.
Cross-site request forgery
Cross-site request forgery is an attack that forces website users to take actions that hackers want them to take. Hackers trick ordinary website users or admins with the help of links in emails or chat messages. If hackers manage to trick website admins, the whole website can be compromised.
Now let’s look through the list of ecommerce website security flaws that can make these attacks happen.
Most common vulnerabilities of ecommerce websites
When making efforts to secure your ecommerce website, you should keep in mind that any malicious action or hacking attack can succeed only if a website has security vulnerabilities. Here, we’ll go through the most typical vulnerabilities that hinder an ecommerce website’s security.
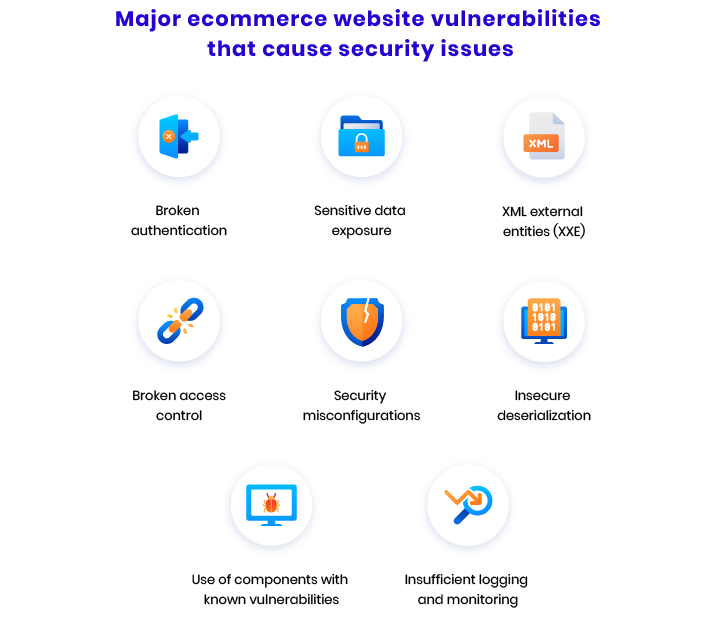
Broken authentication
An incorrect implementation of authentication functionality on your ecommerce website can enable hackers to compromise passwords, security keys, or session tokens of your website users or employees. Because of this vulnerability, malicious users can permanently or temporarily use your visitors’ or employees’ identities and system permissions to perform malicious actions.
It’s possible to get rid of this vulnerability by taking the following steps:
- Use multi-factor authentication
- Avoid using default credentials
- Ensure the use of strong passwords
- Monitor failed login attempts
- Avoid including session IDs in URLs
Sensitive data exposure
Ecommerce companies should take proper measures such as encryption to protect the sensitive information of their website users. For hackers, vulnerable ecommerce websites are the source of user credentials, credit card numbers, and personally identifiable information.
To prevent your users’ data from being exposed, you and your team can take the following actions:
- Use secure sockets layer (SSL) certificates to encrypt data in transit
- Disable caching for user responses containing sensitive information
- Don’t store unnecessary sensitive information
- Encrypt necessary sensitive information at rest
XML external entities (XXE)
Ecommerce websites that parse XML inputs should have a well-configured XML parser in place. Otherwise, external entities can get access to the website’s internal information, files, and ports or even execute malicious code and mount DoS and DDoS attacks.
To ensure your ecommerce website doesn’t have this vulnerability, there are several principles your developers should follow:
- Avoid serialization of potentially sensitive data
- Use relatively simpler data formats such as JSON
- Update XML processors and libraries in a timely fashion
- Implement validation of incoming XML files (XSD validation)
Broken access control
Access control helps to limit a user’s access to only those parts of the website and those actions that are necessary for a particular type of user. Thus, different types of website users — such as admins, registered customers, and non-registered visitors — can have different permissions on your website. If your access control system works incorrectly, it may lead to security breaches.
There are several tips you need to follow to prevent your ecommerce website from having a vulnerable access control system:
- Grant your employees the lowest access levels sufficient to perform their jobs
- Always delete old and unnecessary accounts
- Monitor your website users and employees’ activity
- Disable unnecessary access points
- Block unnecessary activities on the server
Security misconfigurations
Various types of security misconfigurations can lead to dreadful outcomes. If your ecommerce website protection is improperly configured, it’s easier for malicious users to crack it.
To prevent misconfiguration, your team should check that:
- Default security settings aren’t used
- Cloud storage resources aren’t too accessible
- Website security configurations are complete
- HTTP headers are configured correctly
- Error messages don’t contain sensitive data
Insecure deserialization
Deserialization is the opposite of serialization. It entails rebuilding data from some format or byte strings back into an object. Insecure deserialization is when a malicious user inserts malicious data to a website and the website takes it as trusted and deserializes it. This vulnerability can allow hackers to execute malicious code remotely, escalate privileges, and conduct various injection attacks.
The most efficient way to prevent insecure deserialization is to avoid accepting serialized objects from unknown or untrusted sources.
Use of components with known vulnerabilities
Numerous websites all across the internet use open-source components such as libraries and frameworks. If there are any widely known vulnerabilities in an open-source component, it poses a great threat to the websites that use that component.
Your team should continuously scan your ecommerce website components for known vulnerabilities. It’s critical to create and deploy new software patches as soon as vulnerabilities are found.
Insufficient logging and monitoring
When your website becomes a target of hackers, it’s essential to detect the cyberattack on short notice. In 2019, only 47% of businesses managed to detect cyberattacks on their own. The median time it took businesses to detect attackers in their networks was 56 days.
Your company should implement a strong and steady logging and monitoring system to detect and notify you about suspicious activity.
Now that you know what the major threats and software vulnerabilities are, we can proceed to the security checklist that will help you ensure your ecommerce site security.
How to secure your ecommerce website
At RubyGarage, we have a security checklist that helps us easily test each aspect of an ecommerce website’s security. Let’s review the checklist aspect by aspect.
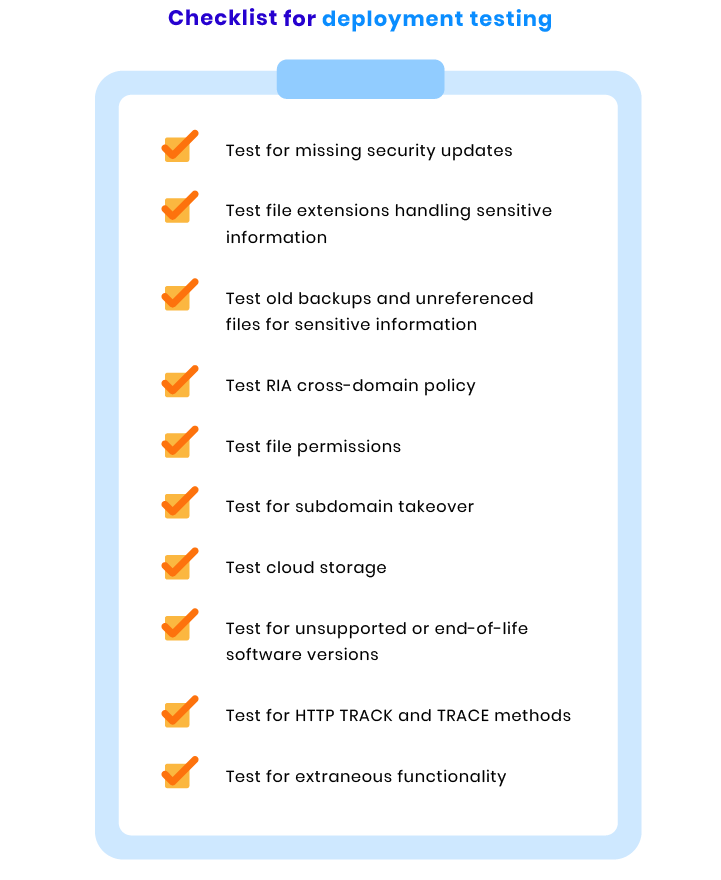
Deployment checks
Deployment is a recurring process and even before your website is released, you need to maintain, update, and improve it. If there are any bugs, your team should find solutions to fix them and update the website as soon as possible. When checking your website for smooth deployment, our team performs the following tests:
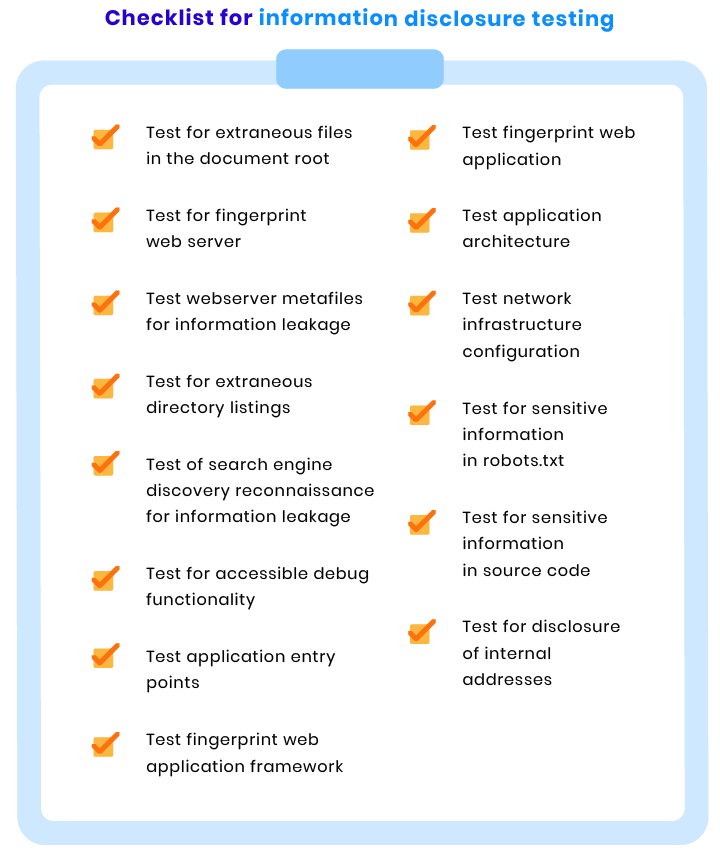
Information disclosure checks
Information disclosure happens when an application isn’t able to properly protect sensitive information from individuals that aren’t supposed to access that information. Information disclosure poses a major threat to website security, as it can be used by attackers to obtain confidential information.
To make sure your web application isn’t prone to information disclosure, we use the following series of tests:
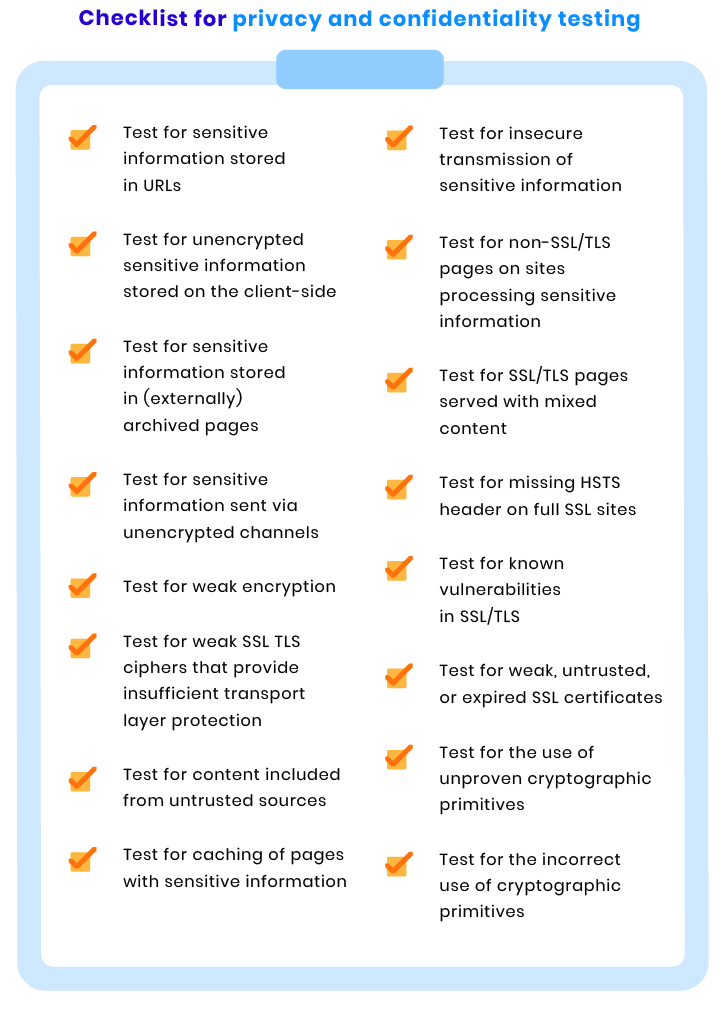
Privacy and confidentiality checks
Protecting your users’ confidential data is vital for your company’s image and credibility. To ensure the privacy of confidential information, our team checks your ecommerce website with the help of the following tests:
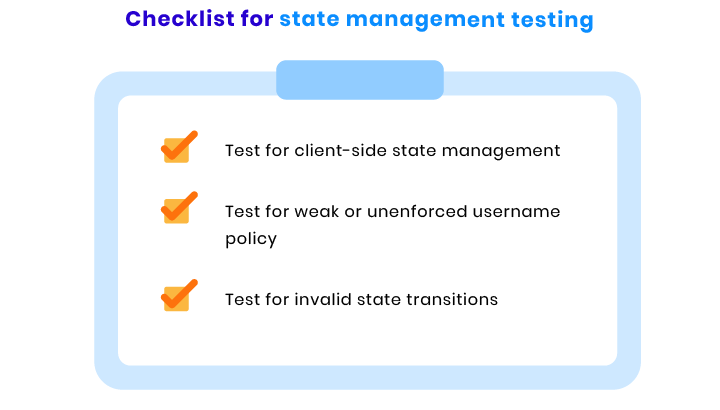
State management checks
Application state management is an essential process that helps you check the condition of your ecommerce website any time you need to. When checking a website’s state management process, we run the tests mentioned below:
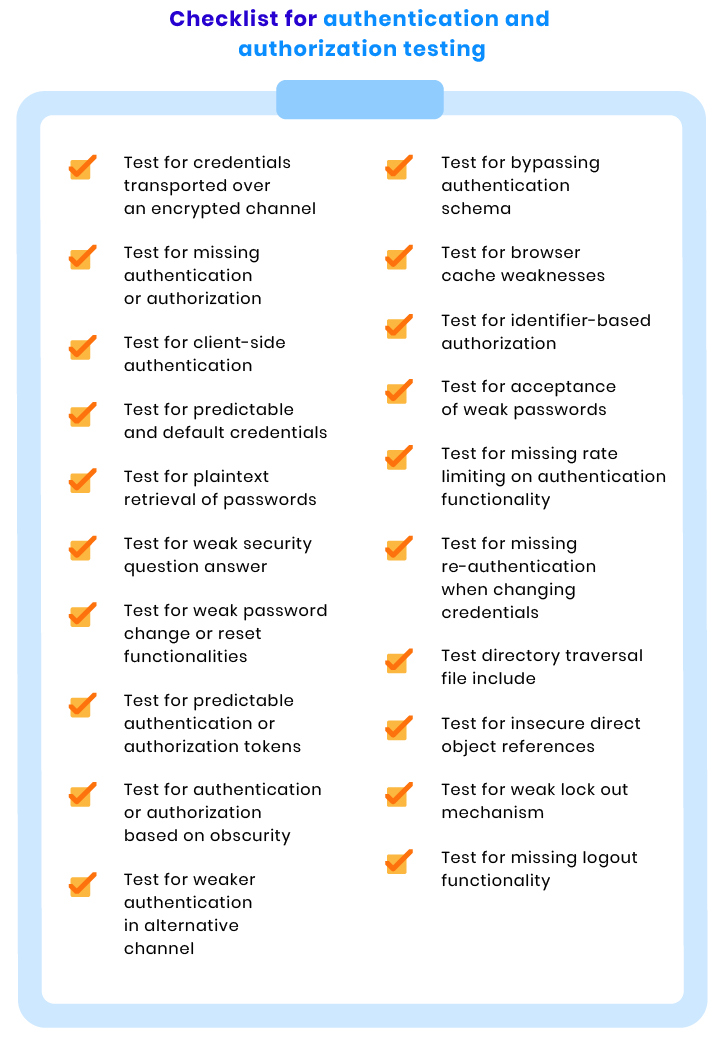
Authentication and authorization checks
Vulnerabilities in authentication can potentially result in user impersonation, which means malicious users can access areas of your website that they’re not supposed to access.
When ensuring your ecommerce website’s security, it’s crucial to check whether your site is prone to vertical or horizontal privilege escalations. Here are the tests that help us check that:
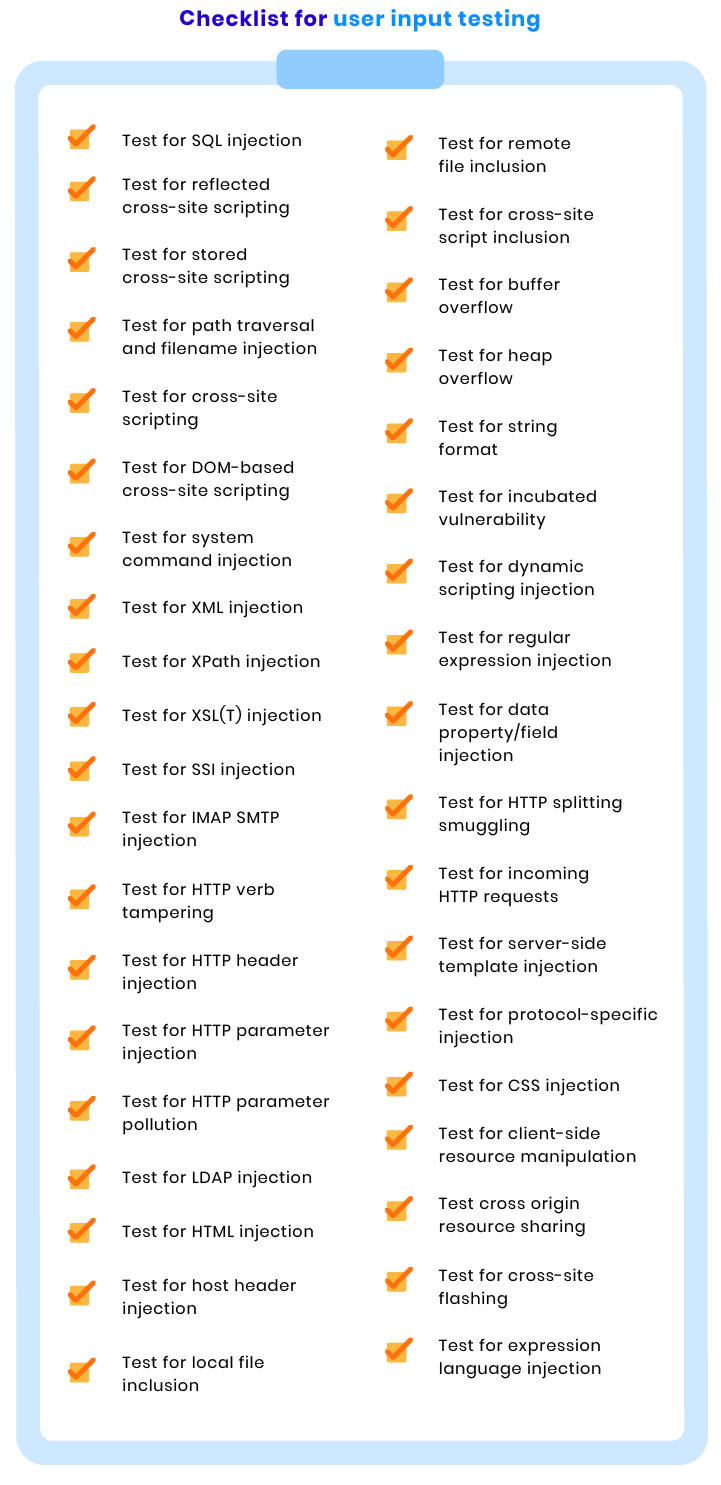
User input checks
Hacker attacks such as SQL injection, cross-site scripting, and malware infections are the result of poor input and output management. At RubyGarage, we check your ecommerce website for input and output management vulnerabilities with the help of the following tests:
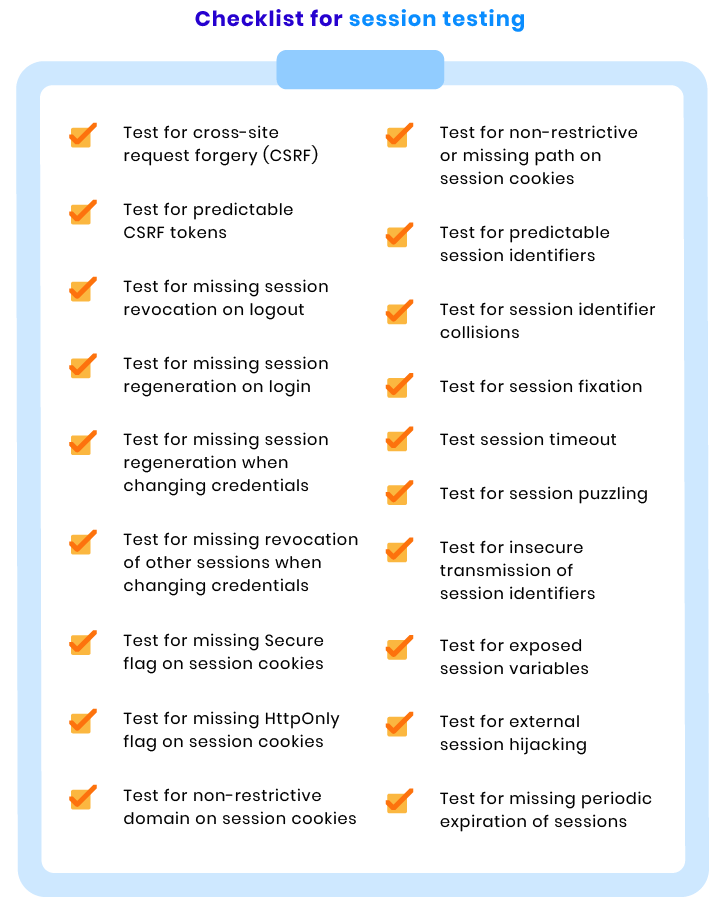
Session checks
Web sessions establish variables such as access rights and localization settings that apply to each interaction a user has with your ecommerce website during the session. With the help of session ID fixation, hackers can hijack legitimate sessions of valid users and use the access rights to accomplish their own goals. To prevent such situations, we conduct the following tests:
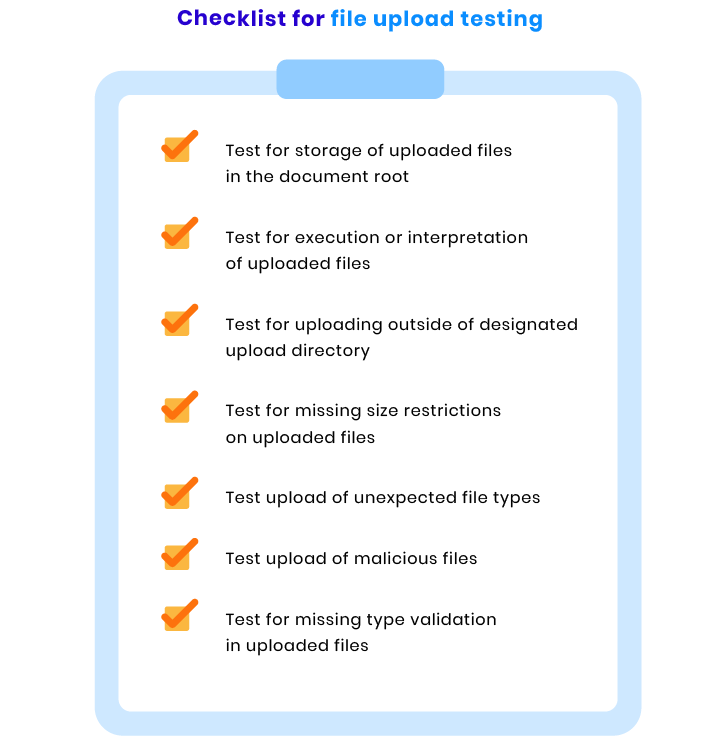
File upload checks
Your website should be able to reject potentially dangerous files to protect its users and information. That’s why your ecommerce website should go through the series of tests mentioned below:
Content checks
Your ecommerce website should have content security policy (CSP) headers in place. These headers give browsers a signal to protect users from dynamic calls that can load malicious content to the webpage. To ensure that CSP headers work appropriately, we perform the following tests:

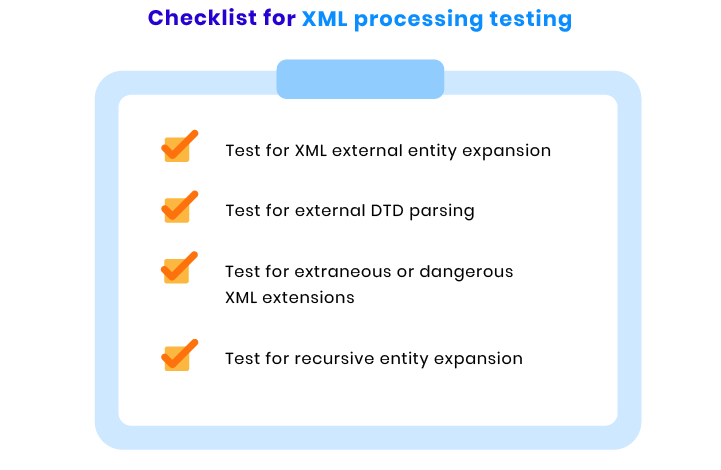
XML processing checks
XML specifications and XML schemas have multiple pitfalls that may lead to different security issues. However, they should be used to ensure the security of XML documents. To make sure malicious users cannot use XML specifications and schemas to brute force your ecommerce website, our team runs the following tests:
Business logic checks
It’s critical to check if your web application logic works the way it should. For instance, such processes as user authentication should be completed in several steps. In case a user takes these steps in an incorrect order or misses one step and still can complete the authentication, there’s definitely an issue with the business logic. Here are the tests we conduct to ensure your website’s logic is correct:
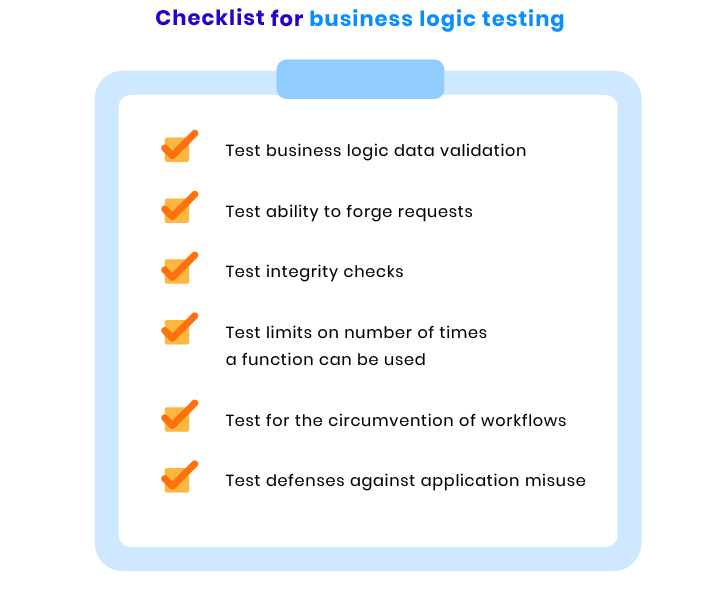
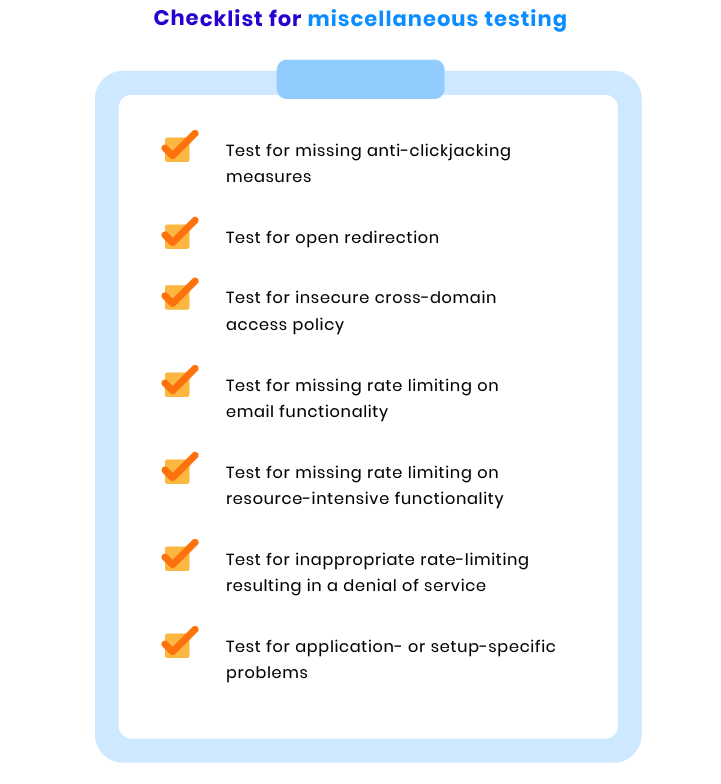
Miscellaneous checks
To ensure the security of your ecommerce site on all fronts, we also conduct the following tests:
Wrapping up
According to Cybersecurity Ventures, the cost of all cybercrimes in the world will reach 10.5 trillion USD annually by 2025. To protect your own ecommerce business now, it’s critical to be aware of all possible threats and secure your ecommerce site by following best practices.
FAQ
-
- Fraud
- Copying
- Hacking attacks
-
- DoS & DDoS attacks
- Brute force attacks
- Cross-site scripting
- SQL injection
- Malware infection
- Cookie theft
- Session fixation
- Cross-site request forgery
-
To ensure the security of an ecommerce website, the RubyGarage team performs a series of security checks:
- Deployment checks
- Information disclosure checks
- Privacy and confidentiality checks
- State management checks
- Authentication and authorization checks
- User input checks
- Session checks
- File upload checks
- Content checks
- XML processing checks
- Business logic checks
- Miscellaneous checks
If you’re looking for a reliable vendor to launch a secure ecommerce website or to ensure the protection of your existing website, contact RubyGarage.











