-
Product Management
Software Testing
Technology Consulting
-
Multi-Vendor Marketplace
Online StoreCreate an online store with unique design and features at minimal cost using our MarketAge solutionCustom MarketplaceGet a unique, scalable, and cost-effective online marketplace with minimum time to marketTelemedicine SoftwareGet a cost-efficient, HIPAA-compliant telemedicine solution tailored to your facility's requirementsChat AppGet a customizable chat solution to connect users across multiple apps and platformsCustom Booking SystemImprove your business operations and expand to new markets with our appointment booking solutionVideo ConferencingAdjust our video conferencing solution for your business needsFor EnterpriseScale, automate, and improve business processes in your enterprise with our custom software solutionsFor StartupsTurn your startup ideas into viable, value-driven, and commercially successful software solutions -
-
- Case Studies
- Blog
Best Practices and Tips to Secure Mobile Banking Apps
The financial sphere is getting more and more attractive for hackers, who are eager to exploit company's every weakness. According to the Identity Theft Record Center’s 2017 data breach report, there were about 70 breaches in the banking, credit, and financial spheres in 2017, with more than two million records exposed.
The importance of security in mobile banking apps can never be neglected. Remember this while designing your own banking app. To help you see the full picture, let’s walk through the most common mobile banking security problems along with tips on how to deal with them by applying modern technologies and approaches.
Top mobile banking app challenges & how to solve them
The following issues are common for all mobile applications regardless of their purpose, though a banking app requires you to be even more diligent and meticulous. Every detail counts when you’re dealing with customers’ sensitive data. Here are the key things to pay attention to when building your banking app security strategy.
1. Insecure data storage
The Norton Cyber Security report by Symantec reveals that more than 140 million Americans were affected by cyber crimes in 2017. Fifty-four percent of them had their personal information involved in a data breach. This is why data storage is such a critical issue nowadays.
Mobile banking apps deal with the most sensitive sort of personal information. They know users’ passwords, account numbers, and credentials that hackers would be happy to get. Such sensitive data cannot be protected sufficiently while stored on a mobile device. Mobile file systems are easily accessible. What’s more, without solid protection, all an adversary needs is a set of specialized instruments to view application data.
At the same time, data leaks can be catastrophic for banks. And material losses aren’t the worst scenario here. Onсe a financial establishment exposes its inability to protect its own customers, clients will leave. Reputation means a lot, if not everything.
Here’s our advice to improve the security of your mobile banking app and store data securely.
Tips to prevent insecure data storage:
- Don’t store users’ personal data and credentials on mobile devices. Once an attacker gets to a physical device, they’ll find a way to hack it and steal the data. It’s best if your app stores everything encrypted in the cloud.
- If you can’t avoid storing data on a mobile device, keep all the information encrypted. Use only the latest and most trustworthy encryption algorithms that make data impossible to decrypt even if intercepted.
- Don’t rely on standard mobile software development kits for iOS and Android. Find proprietary, highly secure storage.

2. Insecure communication
All the communication between a mobile client and a server is conducted by the online connection.
Mobile applications in most cases don’t secure network traffic. This means that a client and a server transmit data over an insecure channel. An unencrypted channel can’t guarantee data integrity.
Another common practice here is to use security protocols only at the stage of authentication but not during the whole session, which is also a mistake. Remember that you need to encrypt all data transferred on backend connections too. Don’t think that a firewall is able to protect data at sufficient scale.
A really secure banking app has to protect all client-to-server connections, server-to-database connections, and other backend connections that pass sensitive data.
Tips to protect data communications:
- Always require SSL chain verification as it’s one of the best standard security technologies for providing an encrypted connection between a web server and a browser, and use the TLS protocol to secure computer networks.
- Don’t use any alternate channels, such as SMS or push notifications, to send sensitive data.
- Choose only the latest and most reliable encryption algorithms that have proved their feasibility, such as Triple DES, RSA, AES, Blowfish, or Twofish.

3. Insecure authentication and authorization
Authentication confirms a user’s identity. Authorization confirms that this user really has access to a particular system. Authentication and authorization prevent attackers from using functionality of the application or backend server.
Modern websites that deal with users’ personal data require users to create long, complex passwords that contain numbers, symbols, and letters. But mobile users prefer four-digit passwords or PIN codes for convenience. App developers know that and often compromise security for users’ comfort. This approach is far from secure.
Tips to avoid insecure authentication and authorization:
- Always use multi-factor authentication. Unlike two-factor authentication, which uses a combination of a username and password in conjunction with a security token linked to a client’s device, multi-factor authentication is much more difficult to circumvent. This approach requires an additional layer of verification such as biometric data confirmation, which isn’t so easy to bypass. Of course, multi-factor authentication is more expensive to implement, but the cost is justified for a banking app.
- Always use server-side authentication and authorization. Offline authentication is not an option as it requires storing data on a mobile device which, as we’ve mentioned, leads to insecure data storage.
- Don’t use such unreliable and easily forged data as geolocation or device identifiers for authentication.

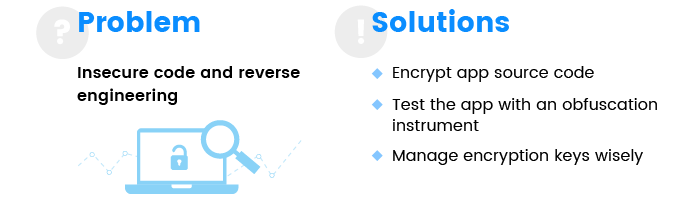
4. Insecure code and reverse engineering
If an app is based on insecure code, it can easily be used to perform illegal operations. That’s why all parts of a banking app need to be protected on every level. In the majority of cases, bugs don’t lead to such severe problems as breaches or data leaks. Still, these imperfections can help hackers achieve their goals.
Reverse engineering is one of the most favored methods of hacking. Reverse engineering involves examining software or its separate components in detail and then subsequently recreating them. Attackers look for apps with insecure code and apply reverse engineering to them. Then they can release a fake app to an app store as the original to collect users’ data or to hack the original application. To avoid this, follow these tips:
Tips to secure code and architecture:
- Encrypt app source code. Not only should users’ personal data be encrypted; the app code should be encrypted as well. Don’t give attackers a chance to copy your app or hack it.
- Always use obfuscation instruments for comprehensive app testing. Imagine that you’re an attacker and try to find all the weak spots in your app.
- Manage your keys wisely. Even the most sophisticated encryption is worth nothing if your keys are easily accessible. Keys have to be stored in a safe place and should be of appropriate length.
Other things you can do
Apart from the tips mentioned above, there are some general security protection methods and recommendations we can provide you with to improve the security of your mobile banking app. Here’s what you need to remember:
1. Watch your employees
It may shock you, but the group responsible for the most data leaks in 2017 was employees.

This is true even though only a small number of workers violated rules consciously to steal or sell data. Among the most widespread employee errors resulting in data leaks, according to the InfoWatch Analytics Center, are the loss of removable media, loss of mobile devices, negligent use of paper documents, and sending of emails to the wrong recipients. Your task is to make sure that employees are aware of the consequences of their behavior.
As a preventive measure, you can sign a Non-Disclosure Agreement with each worker to inform them of their responsibilities. Strong corporate culture and educational lectures can also be helpful.
2. Learn patterns of user behavior
By learning about your customers, you can better identify them and understand how they use your product. Statistics such as a user’s location, speed of entering a password, and channel of authentication can help you detect unusual activity and prevent personal data theft.
User Behavior Analytics, or UBA, is a technology that searches for patterns of use which signal uncommon behavior. UBA is an approach that doesn’t allow you to prevent attacks but that can quickly spot and track hackers’ activity and minimize damage. We highly recommend using UBA as part of your proactive mobile banking app security strategy.
3. Use alerts and notifications
Notifications bring a lot of benefits for your app. Apart from engaging and retaining users, tracking actionable metrics, and improving conversions, push notifications can also be used as a powerful tool to prevent or stop fraud. All you need to do is to inform customers about any suspicious or unusual activity on their accounts and ask them to confirm these actions. In some cases, account blocking can be used as well.
4. Watch your back
The server side of your app is also vulnerable to hacker attacks. That’s why you need to make sure that all APIs, databases, and third-party services that your app has access to are also secure.
Poorly protected APIs give adversaries a chance to bypass authentication and authorization schemes. And databases with no modern security system are like open pockets. Each link of this chain depends on the others, and if one fails in security, then all data is at risk.
As an option, you can use containerization to secure your backend data and documents. Docker containers allow isolating software from its surroundings, which helps to store information more securely.
Final thoughts
Banking apps require the highest level of protection by default. Recent cases of breaches and data leaks have shown how vulnerable mobile apps can be. That’s why you need to think through your online banking mobile security during the planning stage, not the development stage or later.
Make a checklist to be sure that you have all matters figured out and spend enough time testing to exclude any bugs and imperfections.
Don’t forget to subscribe to our blog if you’ve liked this article and you want to get more useful guides and insights from RubyGarage.