-
Product Management
Software Testing
Technology Consulting
-
Multi-Vendor Marketplace
Online StoreCreate an online store with unique design and features at minimal cost using our MarketAge solutionCustom MarketplaceGet a unique, scalable, and cost-effective online marketplace with minimum time to marketTelemedicine SoftwareGet a cost-efficient, HIPAA-compliant telemedicine solution tailored to your facility's requirementsChat AppGet a customizable chat solution to connect users across multiple apps and platformsCustom Booking SystemImprove your business operations and expand to new markets with our appointment booking solutionVideo ConferencingAdjust our video conferencing solution for your business needsFor EnterpriseScale, automate, and improve business processes in your enterprise with our custom software solutionsFor StartupsTurn your startup ideas into viable, value-driven, and commercially successful software solutions -
-
- Case Studies
- Blog
How to Become PCI DSS Compliant: A Complete PCI DSS Requirements Checklist for Your Business
If you run a business that’s somehow connected with processing, transmitting, or storing payment card information, you realize how essential it is to satisfy PCI DSS requirements. PCI DSS compliance offers you a list of significant benefits such as enhanced security of your business, elevated customers' trust, improved operational efficiency, and much more. Keep on reading to get insights into PCI DSS requirements and see if your company meets them
We provide two PCI DSS checklists to help you audit all aspects of your business. One checklist is for the back end and the other is for the front end of your web or mobile application.
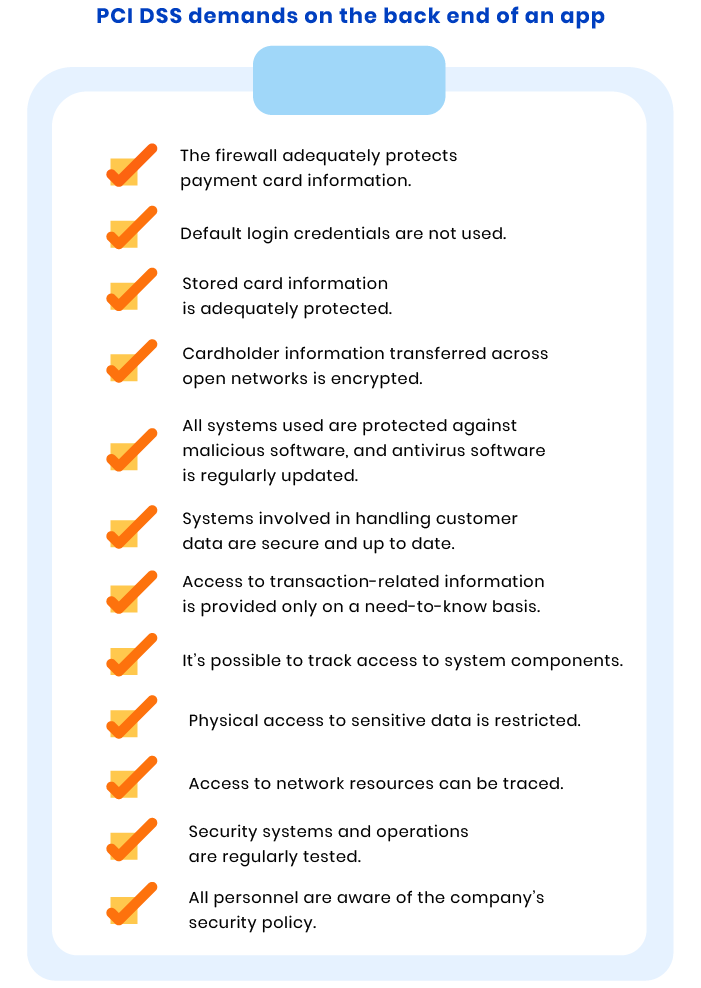
PCI DSS compliance requirements checklist for the back end of an application
Our complete PCI DSS checklist includes security requirements for different areas of your software products and various aspects of your company. We’ll start with PCI DSS requirements for the back end of an application or website.
The firewall adequately protects payment card information
A firewall is the first barrier between the global internet and your computers and servers. Firewalls monitor the data exchanged between computers and servers to check if it’s safe. According to its configuration, a firewall approves or rejects specific data packages.
Firewalls help businesses block unauthorized access to their networks. Your responsibility is to make sure your firewall uses an appropriate setup and to run regular tests to ensure its stability.
Default login credentials are not used
When trying to compromise systems, attackers first try using vendors’ default login credentials. That’s why it’s essential to use unique credentials for all systems.
To ensure compliance with PCI DSS requirements, it’s vital to check that there are no default accounts. You also need to check if new keys are encrypted when changed from the defaults or when a former user of an account changes positions or leaves the company. Moreover, it’s essential to make sure configuration standards are applied to all new systems your company uses.
Stored card information is adequately protected
To ensure the security of stored cardholder data, you need to use various protection methods, which may include encryption, truncation, masking, and hashing.
A compliance audit helps you check if your company has straightforward processes for securely deleting cardholder data, if the data you store satisfies PCI DSS retention policy requirements, and if primary account numbers (PANs) are masked when displayed. Another requirement you must meet is storing cryptographic keys in as few locations as possible.
Cardholder information transferred across open networks is encrypted
It’s critical not only to secure clients’ sensitive information while storing it but also while transmitting it. Data should be appropriately encrypted when in transit across open networks to prevent attackers from getting unauthorized access to it.
To ensure PCI DSS compliance, you should check that only trusted encryption keys and certificates are accepted to access information in transit and should check if security protocols in your company use only secure configurations. Another critical aspect of meeting PCI DSS requirements is whether PANs are masked when sent to end users via messengers.
All systems used are protected against malicious software, and antivirus software is regularly updated
The antivirus software you use in your company should be appropriately configured and kept up to date. Security software must be able to effectively deal with the latest viruses, worms, spyware trojans, rootkits, and adware.
Systems involved in handling customer data are secure and up to date
Vulnerabilities of the systems you use in your workflow may be used by attackers to access your clients’ sensitive data. Software vendors usually eliminate known issues via security patches and updates. That’s why it’s essential to update all software systems used.
Access to transaction-related information is provided only on a need-to-know basis
Human errors are the root cause of 52% of security breaches. That’s why it’s critical to ensure that access to your clients’ sensitive information is provided to as few people as possible. Also, you should provide information to personnel only on a need-to-know basis. You may implement such a policy with the help of clearly defined access controls.
It’s possible to track access to system components
Besides limiting access to sensitive information, you also need to assign a unique identifier to each of your employees to track their actions in your system. This way, you’ll know who accesses stored data and be able to implement an additional level of protection.
You should also ensure the lockout duration is set for each user and that access is revoked right away for employees that leave your company or change positions.
Physical access to sensitive data is restricted
Software protection is, without a doubt, critical for your business. However, hardware threats should not be underestimated.
PCI DSS requirements state that your hardware should be protected by facility entry controls to secure cardholder information. Any hardcopy materials with cardholder information should be shredded to protect them from being reconstructed. The space your hardware is located in should also be fitted with tamper-proof cameras.
Access to network resources can be traced
Tracking tools like log files and system traces should be implemented to easily prevent and detect data breaches. In case of an intrusion, logs enable alerting and analysis, making it easier to identify a security breach. Without logs, you may be unaware of a security breach for a considerable period.
Security systems and operations are regularly tested
To ensure that your security systems provide an appropriate level of protection, you need to perform regular security testing. According to PCI DSS requirements, businesses should run in-house vulnerability checks every quarter. If any security flaws or vulnerabilities are found, they should be addressed immediately.
All personnel are aware of the company’s security policy
Another vital task is to create an internal security policy and explain it to all personnel. Employees should understand the sensitivity of cardholder information and what they need to do to secure and protect it.
PCI DSS requires companies to perform a risk assessment at least once a year and maintain security policies that determine the security responsibilities of all employees.
To become PCI DSS compliant, you need to ensure the security of each aspect of your business. Thus, you should check the security of your mobile application's and web application's front ends.
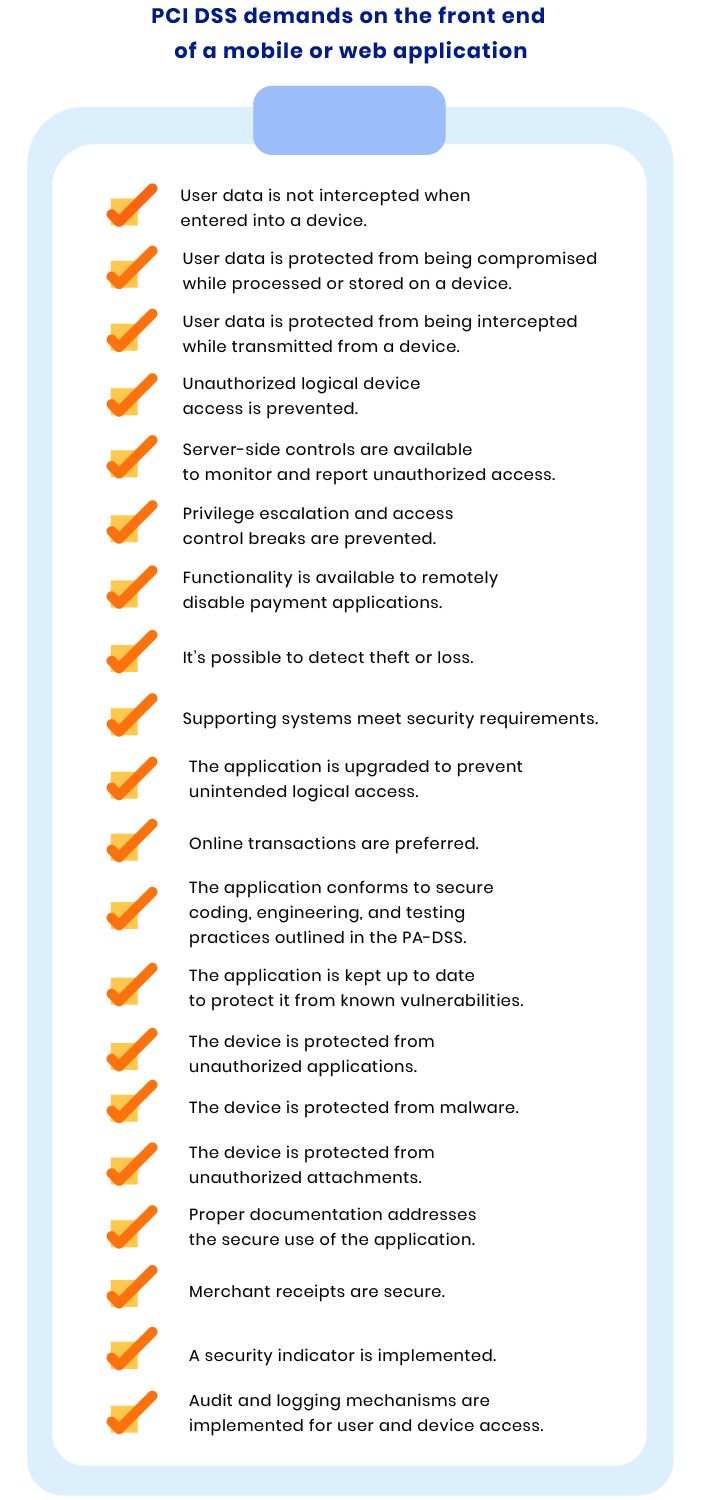
PCI DSS requirements checklist for the front end of a web or mobile application
Let’s see what exactly you need to pay attention to on the front end of a web or mobile application to achieve PCI DSS compliance.
User data is not intercepted when entered into a device
When cardholder data is entered into a device, point-to-point encryption (P2PE) should be used to encrypt it. P2PE is a PCI-validated type of encryption that protects payment card data from the moment of accepting information to the secure point of decryption. If P2PE is not used, end-to-end encryption (E2EE) must be implemented. E2EE is a generic term for secure communication methods that protect data when it’s in transit from one system to another.
User data is protected from being compromised while processed or stored on a device
Sensitive cardholder information should also be protected from leaks when stored on a device. For this purpose, any sensitive information stored on a device should be protected within a secure storage environment. Moreover, after a transaction is authorized, payment card data should be secured with hashing, truncation, or encryption.
User data is protected from being intercepted while transmitted from a device
Cardholder data should be protected with secure encryption while being transferred from a device to another point. Encryption must be provided using the Secure Socket Layer (SSL) or Transport Layer Security (TLS) protocol.
Unauthorized logical device access is prevented
A device must be protected from unauthorized logical access with the help of features like face unlock, passwords, patterns, and PINs. One more useful security feature is forcing a user to re-authenticate after a certain amount of time.
Server-side controls are available to monitor and report unauthorized access
The system should be able to prevent and report unauthorized access. Events like cryptographic key changes, escalation of privileges, and exceeding the maximum available login attempts should be reported.
Privilege escalation and access control breaks are prevented
Controls should be implemented to monitor attempts to jailbreak a device. Jailbreaking is an escalation of privileges that aims to remove restrictions imposed by the software manufacturer. Security controls can initiate alarms and show warnings about jailbreaking both to users and application owners.
Functionality is available to remotely disable payment applications
The system should support functionality allowing a merchant or solution provider to remotely disable a payment application. This functionality should not influence non-payment areas of the device.
It’s possible to detect device theft or loss
A process should exist for identifying the theft or loss of a device. This process may include analysis of GPS data and information about a user as well as device re-authentication at a certain frequency.
Supporting systems meet security requirements
Another step toward achieving PCI DSS compliance is to make sure that all systems involved in the app’s operations also meet PCI DSS requirements.
When you install third-party applications, services, and drivers, do not expect them to be secure. It’s your task to improve their security and ensure they keep your client’s data safe.
To harden third-party systems you’re using in your workflow, you may need, for example, to disable insecure ports, remove particular features, or uninstall certain software.
The application is upgraded to prevent unintended logical access
You should pay a lot of attention to the application’s code and architecture security at the development stage. To prevent security issues, your developers can adhere to development principles such as Security Development Lifecycle, DRY, and SOLID. Also, you can use code obfuscation as a security technique. Obfuscation is a method of hardening application code by introducing intentional sophistication aimed at preventing your software from being cloned and reverse engineered.
Online transactions are preferred
If the payment application is not accessible, the device should not authorize payments offline or store them for later processing.
The application conforms to secure coding, engineering, and testing practices outlined in the PA-DSS
Applications should adhere to secure coding, engineering, and testing principles outlined in the Payment Application Data Security Standard (PA-DSS). Developers and testing engineers should be aware of PCI DSS standards to not only eliminate security issues but prevent them at early stages of the software development lifecycle.
The application is kept up to date to protect it from known vulnerabilities
There should be secure ways of keeping device software and all applications updated through patch management. This helps to protect a device from known vulnerabilities.
Along with this, it should be possible to validate updates and their sources before installation and ensure a timely manner of updating software.
The device is protected from unauthorized applications
The system should block the loading and execution of applications that are not authorized. Also, there should be a process that helps a user differentiate between trusted and unreliable software sources before installing software.
The device is protected from malware
Efficient and reliable anti-malware products such as antivirus software, antispyware, and software authentication programs should be installed and function properly to protect devices against evolving malware.
The device is protected from unauthorized attachments
In case a user’s device is attached to another device (a card reader, for instance) either physically or wirelessly, mutual authentication between the two devices should take place to ensure security.
Proper documentation addresses the secure use of the application
You should provide your clients with instructions on the proper use of the application, including guides on the hardware, operating system, and application software.
Merchant receipts are secure
No matter if you’re sending receipts via email or SMS, all receipts should mask the PAN according to applicable laws and regulations.
A security indicator is implemented
An application must include a function to indicate that payments are processed in a secure state.
Audit and logging mechanisms are implemented for user and device access
A mechanism should be available for auditing and logging user and device access on the merchant’s side. Additionally, there should be clear instructions on how to access logs.
Final thoughts
The PCI DSS requirements checklist we’ve provided here may cause you to think that achieving compliance is too complicated and time-consuming. Although it’s a daunting task, being compliant makes your business safe and secure.
FAQ
-
Backend requirements include the following:
- The firewall can adequately protect payment card information.
- Default login credentials are not used.
- Stored card information is properly protected.
- Cardholder information transferred through open networks is encrypted.
- All systems used are protected against malicious software, and antivirus software is regularly updated.
- Systems involved in handling customer data are secure and up to date.
- Access to transaction-related information is provided only on a need-to-know basis.
- It’s possible to track access to system components.
- Physical access to sensitive data is restricted.
- Access to network resources can be traced.
- Security systems and operations are regularly tested.
- All personnel are aware of the company’s security policy.
-
- User data is not intercepted when entered into a device.
- User data is protected from being compromised while processed or stored on a device.
- User data is protected from being intercepted while transmitted from a device.
- Unauthorized logical device access is prevented.
- Server-side controls are available to monitor and report unauthorized access.
- Privilege escalation and access control breaks are prevented.
- Functionality is available to remotely disable payment applications.
- It’s possible to detect device theft or loss.
- Supporting systems meet security requirements.
- The application is upgraded to prevent unintended logical access.
- Online transactions are preferred.
- The application conforms to secure coding, engineering, and testing practices outlined in the PA-DSS.
- The application is kept up to date to protect it from known vulnerabilities.
- The device is protected from unauthorized applications.
- The device is protected from malware.
- The device is protected from unauthorized attachments.
- Proper documentation addresses the secure use of the application.
- Merchant receipts are secure.
- A security indicator is implemented.
- Audit and logging mechanisms are implemented for user and device access.
-
To achieve PCI DSS compliance, you need to conduct a PCI DSS requirements compliance audit of your company with the help of in-house or external specialists to identify and eliminate soft spots in your software security.
If you’re looking for a team of PCI DSS experts to support you in obtaining PCI DSS compliance, contact RubyGarage to get started today!