-
Product Management
Software Testing
Technology Consulting
-
Multi-Vendor Marketplace
Online StoreCreate an online store with unique design and features at minimal cost using our MarketAge solutionCustom MarketplaceGet a unique, scalable, and cost-effective online marketplace with minimum time to marketTelemedicine SoftwareGet a cost-efficient, HIPAA-compliant telemedicine solution tailored to your facility's requirementsChat AppGet a customizable chat solution to connect users across multiple apps and platformsCustom Booking SystemImprove your business operations and expand to new markets with our appointment booking solutionVideo ConferencingAdjust our video conferencing solution for your business needsFor EnterpriseScale, automate, and improve business processes in your enterprise with our custom software solutionsFor StartupsTurn your startup ideas into viable, value-driven, and commercially successful software solutions -
-
- Case Studies
- Blog
How the Blockchain Works
Throughout history, humanity has tried different ways to exchange values and protect buyers and sellers. After coins, paper money, and banking systems, today’s most obvious solution for exchanging value is electronic payments.
Credit card systems, the internet, and mobile technologies were all important innovations that improved the convenience, speed, and efficiency of transactions. However, in the modern business environment these transaction mechanisms have their shortcomings, including limited transaction sizes, the need for third-party validation, increasing transaction costs, and a weak trust-based model. Besides, fraud and cyberattacks are unavoidable, which also leads to increasing costs for payment operations.
To address these challenges, the world needed a new type of payment system, or rather a network, that could establish trust, remove intermediary institutions (letting any two parties transact directly with each other), eliminate fraud, and provide secure and efficient escrow mechanisms to protect payers and payees. This was the conclusion reached by a person (or persons) known by the pseudonym Satoshi Nakamoto over 11 years ago in 2008 and set out in this white paper.
Satoshi Nakamoto described a solution based on cryptocurrency and a peer-to-peer distributed timestamp server to generate computational proof of the chronological order of transactions.
In this article we’ll define all these terms, explain how these things support blockchain technology, and explain what it takes to build a blockchain network.
What’s a Blockchain?
A blockchain is a shared ledger that stores information about transactions in a distributed manner.
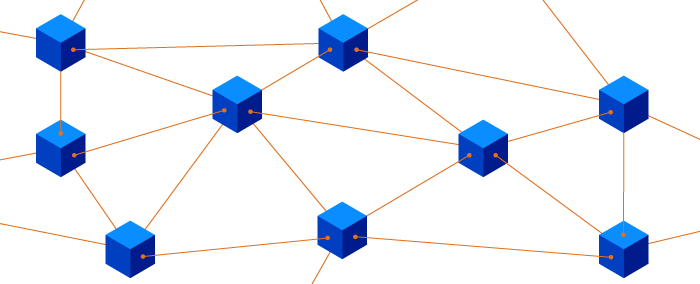
These transactions are performed between people within a blockchain, which is formed by its participants’ computers. These computers provide the computing power to constantly maintain the blockchain (by performing computations and verifying transactions).
Such computers are called nodes, and each node in the network owns a full copy of the blockchain.
How Exactly Does the Blockchain Work?
Technically, a blockchain is a chain of blocks ordered in a network of non-trusted peers. Each block references the previous one and contains data, its own hash, and the hash of the previous block.

Block
A unit of data stored inside a block may be represented by any value depending on the type of blockchain. A block can store an amount of money, a share in a company, a digital certificate of ownership, a vote during an election, or any other value.
A block stores encrypted details about the parties whose interaction resulted in the data stored in the block. A cryptocurrency block also contains the sender’s and receiver’s encrypted identifiers. A block for an ecommerce transaction will contain the identifiers of the retailer and consumer, for example.
Each block also has a hash. This hash is a value generated from a string of text using a mathematical function. A hash can be compared to a fingerprint, as each hash is unique. Its role is to identify a block and the block’s contents.

Once a block is created, a hash is calculated. Changing something inside the block causes the hash to change. So a hash also indicates changes to a block.

Also, each block contains a hash of the previous block. For instance, if there are three blocks in a blockchain, block 3 will contain the hash of block 2, and block 2 will contain the hash of block 1.

If anyone changes the data in a single block, the hash of that particular block changes, but it also makes the whole chain invalid.

A hash is a great tool for identifying attempts to change data in blocks. However, a hash algorithm alone is not enough to ensure the security of a blockchain. To mitigate attempts to corrupt the blockchain and to ensure security, blockchain techmology also uses a process called proof-of-work.
Proof-of-Work
Proof-of-work is a process of producing data that’s hard to get but easy to verify. In the context of a blockchain, proof-of-work is about solving mathematical problems. If a problem is successfully solved, then a new block can be added to the blockchain. On average, performing proof-of-work calculations and adding a new block to the chain takes about 10 minutes.
What’s behind the proof-of-work process?
This mechanism can be compared to a game of dice. Let’s say there’s a specific number – nine, for example – that a player needs to roll. Most likely, the player will need several attempts. But sooner or later, he’ll get nine.
Now let’s add more players to the game. Whoever rolls the correct number first wins.

This is effectively how proof-of-work functions. Of course, in a blockchain the problem that needs to be solved is way more difficult than rolling nine in a game of dice, but the concept is the same.
Computers that form the blockchain network race to solve a mathematical problem to receive a reward and be the first to add the next block to the chain.
Mathematical problems in blockchain have to be hard to solve but easy to check in order to prevent cheating.
Together, hashing and the proof-of-work mechanism ensure the security to the whole blockchain network.
Longest Chain
Since a blockchain consists of an enormous number of nodes, each of them is simultaneously performing proof-of-work. Thus, a situation when several nodes manage to complete proof-of-work with a valid result are pretty common. When this happens it’s called a hard fork, which describes exactly what happens to the blockchain – it forks.

When new blocks are created and added to one of these forked chains, it becomes the longest and again the only valid chain. Blocks from other forked chains get rejected by blockchain nodes, and all the transactions contained in those blocks are sent for verification again.

So far, the longest fork reached is no more than five blocks in a row.
Wallet
Along with hashing and proof-of-work, a blockchain wallet also works to ensure the safety of transactions and prevent fraud. A wallet generates paired public and private keys that further ensure the security of transactions.
A public key can be compared to a postbox. Anyone can put a letter inside of it, but they can’t get that letter back. Only a postal worker who has a private key can open the postbox and get the letter.
This is similar to how keys within a blockchain work. Anyone can send a transaction using a public key to the address of a receiver. This is similar to putting a letter in a postbox. But only the owner of that address who also has the private key can access the value of that transaction.

Distributed Network
Anyone is allowed to join a blockchain peer-to-peer network. When someone joins a network, this person gets a full copy of the blockchain. Distributed storage of data accompanied by effective hashing and proof-of-work mechanisms helps to prevent nearly any fraud.
For instance, in order to add a block containing an invalid hash or invalid data, duplicate an existing block, or perform a fraudulent transaction, an attacker would have to hack the computer of every blockchain participant and slip in the invalid block.

However, even if this were possible, none of the nodes would verify such a block. It would just be ignored, as if it never existed in the first place.
Blockchain Implementation
One of the most popular uses of the blockchain is for cryptocurrency. Cryptocurrencies like Bitcoin, Litecoin, and others aren’t issued or controlled by a central authority. Decentralization allows these blockchain currencies to take the first steps toward an alternative financial model with no intermediaries.
Another area revolutionized by the blockchain is trading and making deals. Traditional contracts are being replaced by smart contracts that are unbreakable, eliminating third parties and working for a wide range of applications: employment contracts, wholesale and retails purchases, agreements for buying property, agreements securing intellectual property rights, insurance, and even marriage contracts. We’ll talk about smart contracts in a separate article.
The blockchain can go far beyond cryptocurrencies and smart contracts, however. The blockchain makes it possible to store, track, and transfer data about real estate objects and land, property rights and medical history, commercial transactions and taxes, and more.
The blockchain is capable of disrupting even such monopolistic spheres as energy management, governance, and law enforcement (as we shared in our recent article on how to implement the blockchain in different business spheres).
Final Thoughts
Gradually, blockchain technology is changing the way we trade, opening new opportunities for individuals and businesses and, aside from its applications in financial services, will become the basis for numerous businesses across industries.
We’re pretty sure that in the right hands, nearly any business idea that’s built on technology can benefit from a blockchain.
If you’re interested in getting more curated content on the blockchain and other emerging technologies, subscribe to our newsletter below.